1. Overview
I found a site that distributes curious PDF converter. The executable file distributed at this site appears to be malicious and have several interesting features.
・ .NET Anti-Analysis
・ Execution of external JavaScript payload with WebView2
・ .NET object manipulation from JavaScript code
This post will mention these techniques.
The execution flow of this executable is shown below.
2. .NET Anti-Analysis
PdfConverters.exe analyzed in this article was created with .NET Core. .NET Core allows developer to embed runtime and libraries into a single executable file. This executable also contains a number of files, which are extracted at execution time into a folder under %TEMP%\PdfConverters. A good way to know the role of these files is to look at [AppName].deps.json. app.deps.json reveals that main functionality of this executable exists in app.dll.
[app.deps.json]
...
"app/1.0.0": {
"dependencies": {
"Microsoft.CodeAnalysis.CSharp": "3.4.0",
"Microsoft.Management.Infrastructure": "2.0.0",
"Microsoft.Web.WebView2": "1.0.1823.32",
"NETStandard.Library": "2.0.3",
"Newtonsoft.Json": "13.0.3",
"runtimepack.Microsoft.NETCore.App.Runtime.win-x86": "3.1.32",
"runtimepack.Microsoft.WindowsDesktop.App.Runtime.win-x86": "3.1.32"
},
"runtime": {
"app.dll": {}
}
},
...
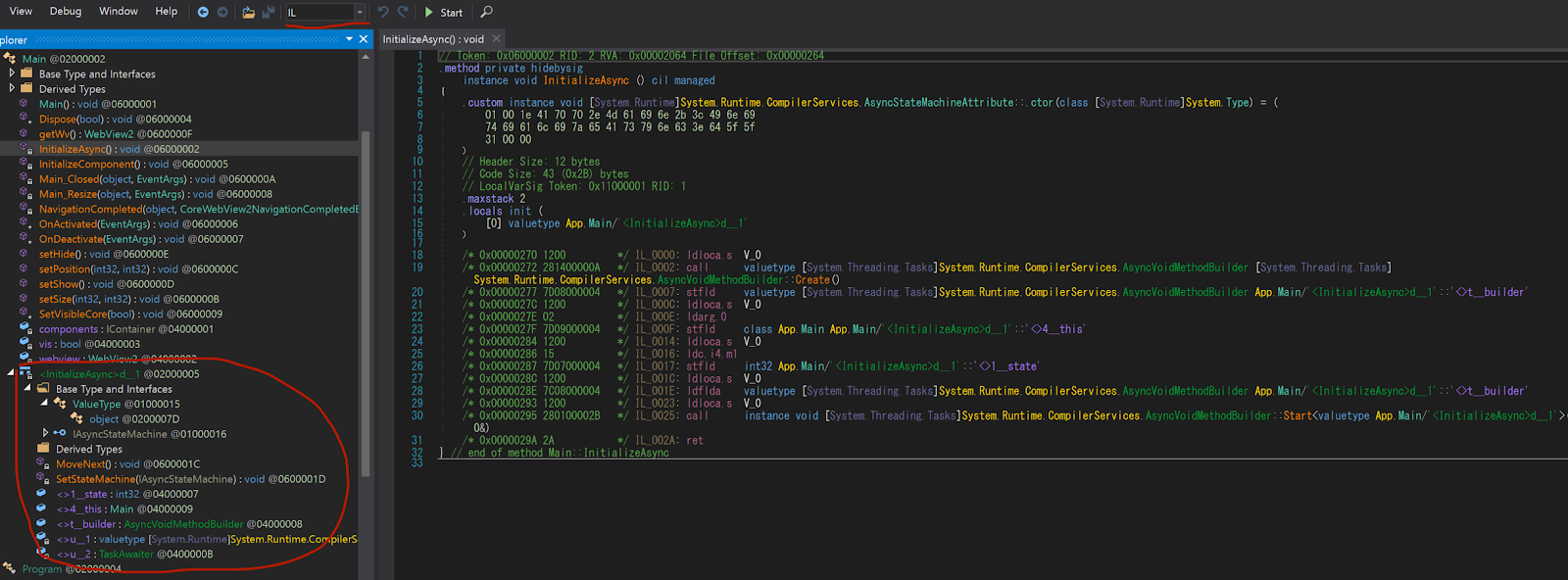
Analysis of app.dll with dnSpy showed that it does not have many methods. However, there was one method whose execution flow was obfuscated. InitializeAsync method is difficult to understand its execution flow, because <InitializeAsync>d__1 is not properly parsed.
When looking at unparsed objects, dnSpy's IL mode is useful. Then I found that MoveNext and SetStateMachine methods are implemented in <InitializeAsync>d__1. This is attacker's System.Runtime.CompilerServices.AsyncStateMachineAttribute interface.
AsyncVoidMethodBuilder.Start takes System.Runtime.CompilerServices.AsyncStateMachineAttribute interface as argument. However, attacker creates fake System.Runtime.CompilerServices.AsyncStateMachineAttribute interface and uses it as AsyncVoidMethodBuilder.Start's argument. This allows MoveNext method to be hidden from the dnSpy's compiled result and to be executed by AsyncVoidMethodBuilder.Start.
https://learn.microsoft.com/en-us/dotnet/api/system.runtime.compilerservices.asyncvoidmethodbuilder.start?view=net-7.0
https://learn.microsoft.com/en-us/dotnet/api/system.runtime.compilerservices.iasyncstatemachine?view=net-7.0
3. Execution of external JavaScript payload with WebView2
PdfConverters.exe uses WebView2 library for external communication. This is technology that allows NET applications to control Microsoft Edge.
https://learn.microsoft.com/en-us/microsoft-edge/webview2/
This executable is accessed to https://www.pdfconvertercompare[.]com/main using WebView2. Why does malware open external page with browser? The general idea is to show the user a decoy page. In fact, this URL distributes the legitimate application.
However, the control of Microsoft Edge by WebView2 was done in invisible mode. Therefore, it has other roles that are not decoys.
I have researched https://www.pdfconvertercompare[.]com/main and noticed main.js script. Although invisible mode, main.js is loaded and executed because it is accessed via Microsoft Edge.
It is probably well known that browser security makes it difficult to impact host OS through JavaScript. Therefore, these methods don't seem to make sense, which will be discussed in the next section.
But if this JavaScript execution is worthwhile, it makes Blue Team's detection difficult. Because external communication is not send by PdfConverters.exe, but by legitimate Microsoft Edge WebView2. This makes detection by EDR and creating IPS/IDS signature difficult.
4. .NET object manipulation from JavaScript code
WebView2 not only allows to control Microsoft Edge from .NET, but also to manipulate .NET objects from JavaScript executed in Microsoft Edge. This executable creates the object of api class and takes it as argument to AddHostObjectToScript method. AddHostObjectToScript method allows manipulation of the argument object from JavaScript.
https://learn.microsoft.com/en-us/microsoft-edge/webview2/how-to/hostobject?tabs=win32
main.js manipulates objects of api class to execute C# code. First, objects of api class can be accessed as chrome.webview.hostObjects.api in JavaScript. This JavaScript code executes LC method with C# code as argument.
...
try {
x = chrome.webview.hostObjects.api
} catch (G9) {}
...
c = '\nusing System;\nusing System.Diagnostics;\n ...' //C# Code
...
v6 = x.LC
...
var Gf = {
a: j,
s: J,
c: vp,
d: vL,
r: vV,
}
var GS = JSON.stringify(Gf)
await vz('8 - before load install search/show overlay assembly')
var GC = await v6(GS, 'a', 's', 'c', 'd', 'r') //Execute api.LC method
...
LC method of api class compiles and executes the given C# code. Each method name, namespace name and class name that takes this operation is given as argument from JavaScript and is not hard-coded into .NET code.
public bool LC(string ja, string ank, string sk, string rck, string rdk, string rfk)
{
JObject jobject = JObject.Parse(ja);
string text = (string)jobject[ank];
if (this.cad.ContainsKey(text))
{
return true;
}
string text2 = (string)jobject[sk]; //C# source code
MemoryStream memoryStream = new MemoryStream();
...
string path = (string)Type.GetType((string)jarray4[0]).GetMethod((string)jarray4[1][0][0]).Invoke(null, null); //System.Runtime.InteropServices.RuntimeEnvironment.GetRuntimeDirectory
...
SyntaxTree syntaxTree = (SyntaxTree)type.GetMethod((string)jarray5[1][0][0], types).Invoke(null, array2); //Microsoft.CodeAnalysis.CSharp.SyntaxFactory.ParseSyntaxTree
...
object obj = type2.GetMethod((string)jarray6[1][0][0], types).Invoke(null, array2); //Microsoft.CodeAnalysis.CSharp.CSharpCompilation.Create
...
obj = method.Invoke(obj, new object[] //Execute compiled C# code
{
obj2
});
...
Using the described techniques, this executable runs C# payload.
PdfConverters.exe : 3DDFA37D2779149114BFDD3E56EFD6573426628639CC6D7E180AA8F15A85C5A2





Comments
Post a Comment